Format-Preserving Encryption
Note
This documentation outlines the in-product format-preserving encryption feature. We continue to support our Snowflake Native App version of format-preserving encryption. Learn more.
ALTR’s format-preserving encryption (FPE) feature is compute-based protection that protects sensitive data at rest while maintaining the usability of the original plaintext. Data can be encrypted directly in your Snowflake account or encrypted upstream (Shift Left) in your source system. FPE ensures that encrypted data has the same format as the original data, so the resulting ciphertext has similar length, alphabet and special characters as the source values, and thus can readily be used as-is in their encrypted state in downstream analytic tools. ALTR manages access to the underlying encryption keys, enabling fine-grained control over decryption while ensuring that your data never leaves your platform.
ALTR’s format preserving encryption supports alphanumeric, alphabetic and numeric data within string columns. ALTR currently requires minimum character length to ensure compatibility with the FF3-1 algorithm. Refer to the following table for details on field alphabet and length support:
Alphabet Type | Characters | Example | Minimum Characters |
|---|---|---|---|
Alphanumeric |
|
| 4 |
Alphabetic |
|
| 4 |
Numeric | 0-9 |
| 6 |
Note
With FPE, ALTR manages encryption key access. Encryption and decryption of data occurs in Snowflake. ALTR does not access your plaintext nor ciphertext when encrypting or decrypting data.
Format-preserving encryption is suited to protect sensitive data such as Personally Identifiable Information (PII) or financial information that meet the minimum value length requirements. The following table outlines examples of data that can be protected using FPE and ciphertext for given alphabets.
Example Data Type | Example Values | Example Ciphertext and Alphabet Type |
|---|---|---|
Social Security Numbers |
|
|
Email Addresses |
|
|
Phone Numbers |
|
|
Encryption and Decryption
Use of NIST standard FF3-1 algorithm for encryption and decryption
Seamless integration with ALTR's Data Access Controls for access control over data decryption
Ability to mask results for users who decrypt data
Usability of ciphertext for common SQL operations and downstream systems via special character preservation and determinism
Ability to encrypt data in Snowflake using a simple user-defined function (UDF) or encrypting data upstream / further left in your data pipeline using the Snowflake REST API
Key Management
Easy key and tweak creation, management and deactivation with ALTR’s UI or REST API
Assignment of and tweaks to individual Snowflake columns for fine-grained access control or Snowflake tags for highly scalable data security
Key naming for easy reference and differentiation across datasets
Key rotation is facilitated without performing an expensive re-encryption of your data
ALTR’s FPE solution supports string (varchar columns) Snowflake data types with alphanumeric, numeric or alphabetic alphabet types.
Note
Note that numbers within string columns are supported, but integer and other numeric data types are not. This is due to the potential of the FPE algorithm generating leading zeroes that would be dropped by Snowflake. For example, if the number 123456 was encrypted and the ciphertext became 012345, Snowflake would remove the leading zero and the value would become 12345. This would result in the wrong plaintext being generated once the data is decrypted.
FPE leverages the encryption keys and tweaks to encrypt data at rest and decrypt data at query runtime. Customers create and manage encryption keys using the ALTR platform. Encryption is performed using a Snowflake user-defined function and decryption is performed using an integration with Snowflake Dynamic Data Masking Policies.
Keys and Tweaks
Both encryption keys and tweaks are required to encrypt and decrypt data using the FF3-1 algorithm. ALTR’s platform enables customers to easily create, manage and deactivate keys and tweaks through an easy-to-use user interface and a REST API.
ALTR’s implementation of the FF3-1 algorithm leverages envelope encryption to afford easy key rotation without the overhead of decrypting and re-encrypting all of the values associated with an encryption key. Envelope encryption involves the use of two layered keys in the encryption process:
Data encryption key (DEK)—the key used to encrypt and decrypt data
Key encryption key (KEK)—the key used to encrypt the DEK
ALTR abstracts the DEK and KEK into a single key object managed by users. When a key object is created by an ALTR user, ALTR generates a DEK and KEK, and encrypts the DEK using the KEK. If a key object is rotated in ALTR, the DEK is decrypted, a new KEK is generated and the DEK is re-encrypted using the new KEK.
Encrypting Data
Note
Encryption and decryption always happens within Snowflake. ALTR’s platform is used for the management and access of encryption keys. ALTR does not access your plaintext or ciphertext data during the encryption or decryption process.
You can encrypt data using ALTR-managed key objects with a Snowflake user-defined function (UDF). When encrypting data, specify the ALTR key, tweak and alphabet to be used for encryption. There are two different routes to encrypt data:
Use the UDF directly to encrypt plaintext data in Snowflake.
Access the UDF via Snowflake’s REST API to encrypt data in systems outside of Snowflake, such as AWS S3 (this method is referred to as Shift Left as it enables users to move the encryption of data left of Snowflake). Using Snowflake’s REST API enables data to move through the ETL process in an encrypted state, ensuring that it is protected during the entire data pipeline.
Decrypting Data
Data is decrypted using ALTR’s integration with Snowflake Dynamic Data Masking Policies and External Functions. This process enables fine-grained access control over which Snowflake users are able to decrypt data back to its original plaintext and which users may only access the encrypted ciphertext data.
ALTR users can mark data for decryption using the ALTR’s platform or the REST API. Decryption can be applied to individual Snowflake columns or to many columns at once through the use of Snowflake object tags. To mark a column or a tag for decryption, it must be connected to ALTR in the encrypted state. When doing so, a user specifies the key, tweak and alphabet type that is used for decryption. Once connected, ALTR creates the necessary masking policy, external function and supporting objects in Snowflake to facilitate decryption.
When users query columns protected with data decryption, Snowflake communicates with the ALTR platform to determine if the user should be able to decrypt the data. If the user is not allowed access to the data in ALTR’s policy engine, only the encrypted ciphertext is returned. If the user is allowed access to the data but in a masked state, the ciphertext is decrypted and then masked based on the policy. If the user is afforded plaintext access from ALTR’s policy, the data is decrypted and the plaintext is returned to the user.
Workflow Example
The following diagram illustrates how to apply FPE to a sample of data and how the policies dictate what different users can see. In the table on the far left, you can see sensitive data in an external stage that contains plaintext emails and SSNs.
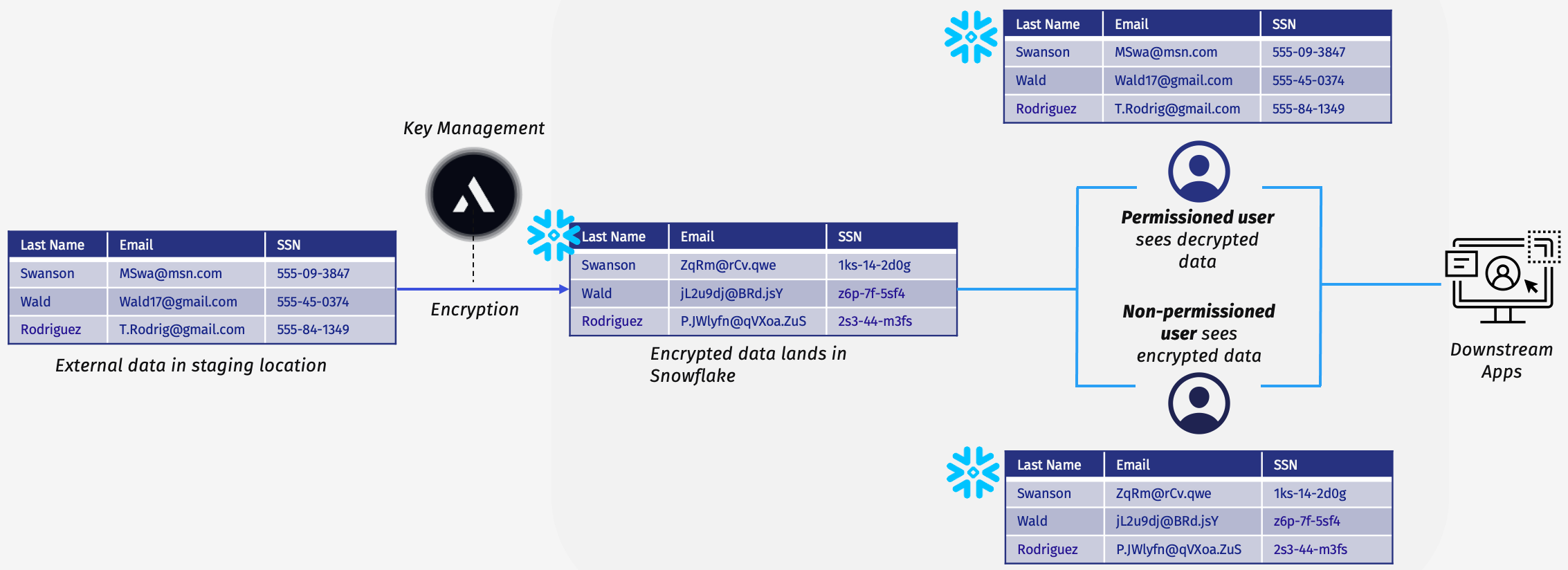
This example shows encryption occurring in the ETL pipeline via the Snowflake REST API. You can see the email and SSN columns both have the expected format but do not contain real values. The final two tables show the different views users see depending on their permissions. A high-privilege user can see the decrypted data, but a low-privilege user only sees the encrypted data. These privileges apply not only directly when querying data in Snowflake but also in any downstream applications.
Key Management Recommendations
Although keys can be reused across many different Snowflake columns to enable ciphertext data inter-compatibility, ALTR recommends minimizing the reuse of encryption key and tweak objects. By keeping a 1:1 or minimal mapping between column/tag and keys/tweaks, you can minimize the risk of an unauthorized user discovering unwanted connections between two different datasets or a compromised key being used to decrypt other unrelated data.
Format-Preserving Encryption Example
Let's say you have a column containing social security numbers such as 111-11-1111 and you want to encrypt it using FPE.
Create key and tweak objects named the following:
Key: mySecretKey
Tweak: myTweak123
Call the encryption UDF using mySecretKey, myTweak123 and the numeric alphabet type to encrypt the social security number column, resulting in ciphertext like 123-45-6789.
You want to conditionally decrypt the data using ALTR. Connect the column in the encrypted state, specifying the key (mySecretKey), tweak (myTweak123) and alphabet type (numeric) used to encrypt the data. You create an ALTR access control policy specifying that your Snowflake user can access that column without masking applied. When you query the data, you are returned the original decrypted social security numbers such as 111-11-1111.
To set up format-preserving encryption:
Enable FPE for your organization by contacting ALTR Support.
Connect a Snowflake data source to ALTR. If your data source was connected before January 2025, either connect a new data source within the same Snowflake account or disconnect and reconnect your data source before proceeding or contact ALTR Support for assistance. Learn more.
Use the
ALTR_DSAAS_DB.ALTR_DSAAS_$<ORGID>.ALTR_FPE_ENCRYPT(...)user-defined function, key, tweak and alphabet type to encrypt your data in Snowflake. Learn more.Note
To encrypt data in your source system before it enters the ETL pipeline (i.e., shifting left), contact ALTR Support for assistance.
Connect the encrypted column or tag in ALTR. Specify the key, tweak and alphabet type used for encryption.
Decrypt data either with an access control policy or with a UDF.
Enable FPE
Format-preserving encryption is an add-on feature for ALTR. To purchase this add-on feature and to enable it on your organization, contact ALTR Support.
Manage Keys and Tweaks
Before connecting encrypted columns to ALTR, create a key and a tweak. A key is used to encrypt and decrypt data and ensures different encryption results for the same data. A tweak is an additional value that modifies the encryption process by adding variability and security. ALTR’s FPE feature uses envelope encryption, which is the process of encrypting data with a key and then encrypting the key with another key. Learn more.
Create Keys
To strengthen the security of the encryption, we recommend using separate keys and tweaks for different datasets and minimizing key reuse. For example, have separate keys and tweaks for city and state. Using a different key (and tweak) for each type of data ensures that all of your PII isn’t exposed if your key is compromised.
To create a key:
Select Key Management in the Navigation menu.
Click Create Key.
Enter a Key Name. Key names are unique and case sensitive. Ensure the key name
has 256 or fewer characters
does not have leading or trailing spaces
Click Save.
Rotate a key as a preventative steps to reduce the threat of the key being compromised. We recommended rotating the key every 3-6 months and after a suspected incident. Keys can be rotated one at a time and every 30 minutes.
If a key has been compromised, rotating it is not enough of a security measure. We recommend that you deactivate the key and create a new one. Learn more.
This process rotates the key encryption key (KEK) in order to enhance security and maintain the integrity of the data encryption process, meaning, it changes the key that is used to encrypt the data encryption key (DEK) via envelop encryption. Learn more.
To rotate a key:
Select Key Management in the Navigation menu.
Click the key you wish to rotate.
Click Rotate Key; the Rotate key? modal displays.
Click Rotate Key to confirm.
Deactivate a key if
it is no longer being used.
you suspect the key has been compromised.
Deactivating a key prevents users from accessing data; you will be unable to encrypt or decrypt data once the key is deactivated. You will be locked out of your data, so be sure to update the key on the column or the tag before deactivating the key.
Once a key is deactivated, it cannot be reactivated using the ALTR platform; you must contact ALTR Support to reactivate the key.
Note
If an encrypted column or tag is connected to ALTR with a deactivated key, you won’t be able to decrypt the data.
To deactivate a key:
Ensure the key is not in use on an encrypted tag or column. If the key is in use,
Decrypt the data in Snowflake using the existing key and tweak.
Create a new key in ALTR.
Re-encrypt the data in Snowflake using the new key and existing tweak.
Update the relevant column or tag connected in ALTR using the new key and existing tweak.
Note
A key can be changed on an existing column. However, you are unable to update a connected tag in ALTR; disconnect the tag from ALTR and reconnected it with the new key.
Select Key Management in the Navigation menu.
Click the key you wish to deactivate.
Click Deactivate Key; the Deactivate key? modal displays.
Click Deactivate Key to confirm. The key still exists, but cannot be used to encrypt a column or a tag.
Reactivate a key if you
wish to use it again.
no longer suspect the key has been compromised.
To reactivate a key, contact ALTR Support.
Create Tweaks
To strengthen the security of the encryption, we recommend using separate keys and tweaks for different datasets and minimizing key reuse. For example, have separate keys and tweaks for city and state. Using a different key (and tweak) for each type of data ensures that all of your PII isn’t exposed if your key is compromised.
To create a tweak:
Select Key Management in the Navigation menu.
Click the Tweaks tab.
Click Create Tweak.
Enter a Tweak Name. Tweak names are case sensitive. Ensure the tweak name
has 256 or fewer characters
does not have leading or trailing spaces
Click Save.
Deactivate the tweak if you suspect it has been compromised. You will be unable to encrypt or decrypt data with this tweak once it is deactivated.
Before deactivating a tweak, ensure it is not in use by a column or a tag for encryption. You won't be able to decrypt a tag or column if it is associated with a deactivated tweak.
To deactivate a tweak:
Ensure the tweak is not in use on an encrypted tag or column. If the tweak is in use,
Decrypt the data in Snowflake using the existing key and tweak.
Create a new tweak in ALTR.
Re-encrypt the data in Snowflake using the new tweak and existing key.
Update the relevant column or tag connected in ALTR using the new tweak and existing key.
Note
A tweak can be changed on an existing column. However, you are unable to update a connected tag in ALTR; disconnect the tag from ALTR and reconnect it.
Select Key Management in the Navigation menu.
Click the tweak you wish to deactivate.
Click Deactivate Tweak; the Deactivate tweak? modal displays.
Click Deactivate Tweak to confirm. The tweak still exists, but cannot be used to encrypt a column or a tag.
Reactivate a tweak if you
wish to use it again.
no longer suspect the tweak has been compromised.
To reactivate a tweak, contact ALTR Support.
To ensure data is protected at rest, both existing records and any new loaded data must be encrypted. Data can be encrypted directly in Snowflake or encrypted in data pipelines prior to being loaded in Snowflake. ALTR encryption is available in Snowflake as a User-Defined Function (UDF), which can be called in a variety of ways to encrypt data. Users can call the UDF directly in Snowflake, call the UDF from outside tools (such as ETL) via Snowflake’s REST API or call the UDF on incrementally loaded data using Snowflake Streams and Tasks. Each of these requires different considerations and configuration.
Once the data is encrypted, you can then apply policy. Contact ALTR Support for assistance in encrypting columns in Snowflake.
Decryption occurs in Snowflake. Once you set up policy on the encrypted data, as you query data, ALTR is used to decrypt it depending on your role, the key and tweak. Learn more.
Note
Optionally, you can encrypt an array of data. Learn more.
ALTR recommends encrypting data directly in source systems, or during the ETL process, to ensure that records are never stored unencrypted in Snowflake.
Warning
Encrypting causes data transformation into the specified encryption alphabet. Snowflake objects that prevent transformation, such as shared tables, and functions that expect certain string patterns, such as collation, may not work with FPE.
Before encrypting data
Ensure that a tweak and key have been created in the ALTR platform.
If calling the user-defined function, verify you have the USAGE privilege on the fully qualified function (
ALTR_DSAAS_DB.ALTR_DSAAS_<ORGID>.ALTR_FPE_ENCRYPT(VARCHAR, VARCHAR, VARCHAR, VARCHAR)), schema (ALTR_DSAAS_DB.ALTR_DSAAS_<ORGID>)and database (ALTR_DSASS_DB).Note
Replace
<ORGID>with your ALTR organization ID. Copy this ID from your Snowflake account or from the ALTR platform (select → → ) Learn more. If copying the organization ID from the ALTR platform, update the format by replacing hyphens with underscores and converting all letters to uppercase.Replace
<Role>with the role that will be used to execute the function. You must execute the following commands with a role that has the MANAGE GRANTS privilege.
GRANT USAGE ON FUNCTION ALTR_DSAAS_DB.ALTR_DSAAS_<ORGID>.ALTR_FPE_ENCRYPT(VARCHAR, VARCHAR, VARCHAR, VARCHAR) TO ROLE <Role>;
GRANT USAGE ON DATABASE ALTR_DSAAS_DB TO ROLE <Role>;
GRANT USAGE ON SCHEMA ALTR_DSAAS_DB.ALTR_DSAAS_<OrgID> TO ROLE <Role>;
If using Snowflake’s REST API, ensure that the rest API has permission to the database, schema, table and function above.
For first-time encryption and/or static datasets, ALTR’s encrypt UDF can be called on a set of data to encrypt in bulk. This can be especially useful when familiarizing yourself with FPE in a non-production environment, as the UDF can be easily called without need to integrate with third-party tools or creating separate stream and task objects.
Caution
Be careful not to double-encrypt Snowflake records. If the same value is encrypted twice, it cannot be fully decrypted using ALTR policy.
This following series of calls encrypts every value in the specified column using the specified key, tweak and alphabet. This can be useful when first encrypting data or after truncating and re-loaded records in a table.
To bulk encrypt an entire column via UDF:
Define the key and tweak names for encryption. Key name is case sensitive.
SET KEY_NAME = '<Insert Key Name Here>'; -- Replace with the name of your encryption key SET TWEAK_NAME = '<Insert Tweak Name Here>'; -- Replace with the name of your tweak key
Specify the alphabet for encryption. Options are: alphabetic, numeric or alphanumeric.
SET ALPHABET = 'alphabetic' | 'numeric' | 'alphanumeric';
Encrypt the specified column in the target table using FPE.
Replace
<DATABASE>, <SCHEMA>, <TABLE>and<COLUMN>with the names of your database, schema, table and column, respectively.Replace
<ORGID>with the your ALTR organization ID. Copy this ID from your Snowflake account or from the ALTR platform. Learn more.Note
If copying the organization ID from the ALTR platform, update the format by replacing hyphens with underscores and converting all letters to uppercase.
UPDATE "<DATABASE>"."<SCHEMA>"."<TABLE>" SET "<COLUMN>" = ALTR_DSAAS_DB.ALTR_DSAAS_<ORGID>.ALTR_FPE_ENCRYPT( "<COLUMN>", -- Column to encrypt $KEY_NAME, -- Name of the encryption key. $TWEAK_NAME, -- Name of the tweak. $ALPHABET -- Character set for FPE );
This following series of calls encrypts an array of individual records. This can be be useful when testing encryption or encrypting records as a part of an ETL pipeline.
This series of calls call encrypts every value in the specified column using the specified key, tweak and alphabet.
To bulk encrypt an array of records via UDF:
Define the key and tweak names for encryption. Key name is case sensitive.
SET KEY_NAME = '<Insert Key Name Here>'; -- Replace with the name of your encryption key SET TWEAK_NAME = '<Insert Tweak Name Here>'; -- Replace with the name of your tweak key
Specify the alphabet for encryption. Options are: alphabetic, numeric or alphanumeric.
SET ALPHABET = 'alphabetic' | 'numeric' | 'alphanumeric';
Encrypt the specified column in the target array using FPE. Replace
<ORGID>with the your ALTR organization ID. Copy this ID from your Snowflake account or from the ALTR platform. Learn more.Note
If copying the organization ID from the ALTR platform, update the format by replacing hyphens with underscores and converting all letters to uppercase.
SET ENCRYPT_ARRAY = '["value1", "value2", "value3"]'; SELECT ALTR_DSAAS_DB.ALTR_DSAAS_<ORGID>.ALTR_FPE_ENCRYPT_ARRAY( $ENCRYPT_ARRAY, -- Array to encrypt $KEY_NAME, -- Name of the encryption key. $TWEAK_NAME, -- Name of the tweak. $ALPHABET -- Character set for FPE );
To maintain encryption within a table, any additional loaded records must be encrypted with the same key, tweak and alphabet used for initial encryption. Although the recommended method is to encrypt incremental loads via ETL integration, the following workflows enable you to directly encrypt additionally loaded records in Snowflake. These examples leverage WHERE clauses to ensure that data is not doubly encrypted.
This process identifies targeted records in a column via a WHERE clause and encrypts them using the specified key, tweak and alphabet.
To encrypt via UDF:
Define the key and tweak names for encryption. Key name is case sensitive.
SET KEY_NAME = '<Insert Key Name Here>'; -- Replace with the name of your encryption key SET TWEAK_NAME = '<Insert Tweak Name Here>'; -- Replace with the name of your tweak key
Specify the alphabet for encryption. Options are: alphabetic, numeric or alphanumeric.
SET ALPHABET = 'alphabetic' | 'numeric' | 'alphanumeric';
Encrypt the specified column in the target table using FPE.
Replace
<DATABASE>, <SCHEMA>,<TABLE>and<COLUMN>with the names of your database, schema, table and column, respectively.Replace
<ORGID>with the your ALTR organization ID. Copy this ID from your Snowflake account or from the ALTR platform. Learn more.Note
If copying the organization ID from the ALTR platform, update the format by replacing hyphens with underscores and converting all letters to uppercase.
Replace CONDITION with the logic that identifies unencrypted records. For example, if you have a “LOAD_DATE” column, you can set this condition to only apply to records from the latest data load.
UPDATE "<DATABASE>"."<SCHEMA>"."<TABLE>" SET "<COLUMN>" = ALTR_DSAAS_DB.ALTR_DSAAS_<ORGID>.ALTR_FPE_ENCRYPT( "<COLUMN>", -- Column to encrypt $KEY_NAME, -- Name of the encryption key $TWEAK_NAME, -- Name of the tweak $ALPHABET -- Character set for FPE ) WHERE <CONDITION>;
This process leverages Snowflake Streams and Tasks to automatically encrypt new records within a table. The Snowflake stream keeps track of newly loaded records and the task occasionally inspects the stream and encrypts any newly loaded data. Note that loaded data exists unencrypted until the task executes.
To encrypt via Snowflake Streams and Tasks:
Create a Snowflake Stream to capture changes on the desired table. Provide a name for the stream, and replace
<DATABASE>, <SCHEMA and <TABLE>with the appropriate Snowflake object namesCREATE STREAM "DATABASE"."SCHEMA"."STREAM" ON TABLE "DATABASE"."SCHEMA"."TABLE";
Create and enable a Snowflake Task that consumes from the stream and automatically encrypts records in the table. Provide a name for the task, specify a warehouse and schedule for the task, and update
<DATABASE>, <SCHEMA>,<TABLE>,STREAMand<COLUMN>with the names of the appropriate schema objects.CREATE OR REPLACE TASK "<DATABASE>"."<SCHEMA>"."TASK_NAME" WAREHOUSE = "WHAREHOUSE" SCHEDULE = '5 MINUTE' AS MERGE INTO "<DATABASE>"."<SCHEMA>"."<TABLE>" AS T USING "<DATABASE>"."<SCHEMA>"."<STREAM>" AS S ON T.ID = S.ID -- match to primary key WHEN MATCHED AND S.METADATA$ACTION = 'INSERT' THEN UPDATE SET T."<COLUMN>" = ALTR_DSAAS_DB.ALTR_DSAAS_<ORGID>.ALTR_FPE_ENCRYPT( S."<COLUMN>", $KEY_NAME, $TWEAK_NAME, $ALPHABET ); ENABLE TASK "<DATABASE>"."<SCHEMA>"."TASK_NAME"Note
If copying the organization ID from the ALTR platform, update the format by replacing hyphens with underscores and converting all letters to uppercase.
Note
Setting the SCHEDULE for more frequent execution will enable for more frequent encrypting, minimizing the window in which records remain unencrypted, but will increase warehouse utilization.
Data can be encrypted as a part of your Extract, Transform and Load process (ETL, or ELT) either by calling the UDF directly in Snowflake on loaded data or before data load via Snowflake’s REST API. There are also some open source solution accelerators available for integration with specific ETL tools. The mechanism for encrypting data during the ETL pipeline depends on the tool(s) being used and your configured workflows. Reach out to ALTR Support for assistance on integrating encryption in your ETL pipeline.
ALTR uses the FF3-1 algorithm to perform format-preserving encryption (FPE). However, FF3-1 has a minimum length requirement in order to work securely, so it can’t encrypt values that are too short.
This affects common data like short names (“Sam”), state abbreviations (“TX”) or ZIP codes (“78701”), which aren’t long enough on their own. Padding adds extra characters to meet the required length so that encryption can be successful.
To solve this, ALTR provides an optional padding feature that allows customers to add characters to short values before encryption: 4 characters for alphabetic or alphanumeric data, and 6 characters for numeric data. However, padding introduces tradeoffs that may impact either the security or usability of your encrypted data.
Caution
Before you can pad data during encryption using ALTR, contact your Account Representative to enable this feature.
Use padding when:
Your data does not meet the minimum length requirement for FF3-1. Learn more.
You need to encrypt values consistently across systems and maintain referential integrity (deterministic padding).
You need to protect short sensitive values where encryption would otherwise fail without padding.
Be cautious about padding when:
You are encrypting highly sensitive, short data and want the strongest possible protection. Deterministic padding makes it easier for attackers to infer patterns.
You don’t need padding, i.e., your values already meet FF3-1's minimum length requirement.
Deterministic Padding
Deterministic padding uses the same padding characters each time. The result is predictable: the same input always results in the same ciphertext.
Use | Pros | Cons | Example |
|---|---|---|---|
When maintaining queryability is more important than maximizing security | Useful when referential integrity is critical |
| Plaintext: Padded: Encrypted: |
Non-Deterministic Padding
Non-deterministic padding adds random characters before encryption. The same plaintext encrypts differently each time.
Use | Pros | Cons | Example |
|---|---|---|---|
When maximum security is required and the data doesn’t need to be queried post-encryption. |
| Breaks determinism | Plaintext: Run 1 → Padded: Encrypted: Run 2 → Padded: Encrypted: |
To encrypt padded data:
Define the key and tweak names for encryption. Key name is case sensitive.
SET KEY_NAME = '<Insert Key Name Here>'; -- Replace with the name of your encryption key SET TWEAK_NAME = '<Insert Tweak Name Here>'; -- Replace with the name of your tweak key
Specify the alphabet for encryption. Options are: alphabetic, numeric or alphanumeric.
SET ALPHABET = 'alphabetic' | 'numeric' | 'alphanumeric';
Encrypt the specified column in the target table using FPE.
Update the
PADDING_TYPEto eithernondeterministicordeterministic. Learn more.Replace
<DATABASE,<SCHEMA>,<TABLE>and<COLUMN>.Replace
<ORGID>with the your ALTR organization ID. Copy this ID from your Snowflake account or from the ALTR platform. Learn more.Note
If copying the organization ID from the ALTR platform, update the format by replacing hyphens with underscores and converting all letters to uppercase.
SET PADDING_TYPE = 'nondeterministic' | 'deterministic' ; UPDATE "<DATABASE>"."<SCHEMA>"."<TABLE>" SET "<COLUMN>" = ALTR_DSAAS_DB.ALTR_DSAAS_<ORGID>.ALTR_FPE_ENCRYPT( "<COLUMN>", -- Column to encrypt $KEY_NAME, -- Name of the encryption key. $TWEAK_NAME, -- Name of the tweak. $ALPHABET, -- Character set for FPE $PADDING_TYPE );
Once columns have been encrypted in Snowflake, connect the encrypted columns to ALTR in order to apply masking policies to define who is able to view the decrypted data. Encrypted columns are connected to ALTR individually.
Note
If your encrypted column is already connected in ALTR, update the column to mark it as encrypted.
To connect an encrypted column to ALTR:
Ensure the column has been encrypted in Snowflake. Learn more.
Select → in the Navigation menu.
Click the Columns tab.
Click Connect Column.
Select the Data Source in which the column resides.
Select the Schema and Table or View in which the column resides.
Select the Column.
Note
If your schema information doesn't display in the dropdowns, ensure your service user account has privileges to access the data.
Select Format-preserving encryption from the Which option applies to this column? dropdown.
Select a Key. This is the main key to encrypt and decrypt the column and is added on the Key Management page. Learn more.
Select a Tweak. This is the additional value that adds variability and security to encrypt and decrypt the column. Tweaks are added on the Key Management page. Learn more.
Select an Alphabet Type that pertains to the data you have encrypted. Options are:
Alphabetic—encrypted data is only letters: a-z and A-Z
Alphanumeric—encrypted data is letters and numbers: a-z, A-Z and 0-9
Numeric—encrypted data is only numbers: 0-9
(Optional) Enable Encrypted with padding if the column was padded before encryption. Padding may compromise the security or usability or protected data. Learn more.
Click Connect Column.
Once tags have been encrypted in Snowflake, connect the encrypted tags to ALTR in order to apply masking policies to define who is able to view the decrypted data. Encrypted tags are connected to ALTR individually.
Note
Connected tags cannot be edited in ALTR. If your encrypted tag is already connected to ALTR and you need to mark it as encrypted:
Disconnect the tag from ALTR.
Reconnect the tag to ALTR. Mark the tag as containing encryption and assign a key and a tweak.
To connect an encrypted tag to ALTR:
Ensure the tag has been encrypted in Snowflake. Learn more.
Select → in the Navigation menu.
Click the Tags tab.
Click Connect Tag.
Select a ALTR Data Source Connection. This can be any data source associated with your Snowflake account where the Service user has privileges to access the tag’s database.
Select a Tag Database. This is the database where the tag is located and can be different from the data source connection.
Select a Tag Schema. This is the schema within the Tag Database where the tag is located.
Select a Tag Name. This is the name of the tag in Snowflake.
Note
If your data doesn't display in the dropdowns, ensure your service user account has privileges to access the data.
Select Format-preserving encryption from the Which option applies to this tag? dropdown.
Select a Key. This is the main key to encrypt and decrypt the tag and is added on the Key Management page. Learn more.
Select a Tweak. This is the additional value that adds variability and security to encrypt and decrypt the tag. Tweaks are added on the Key Management page. Learn more.
Select an Alphabet Type. Options are:
Alphabetic—encrypted data is only letters: a-z and A-Z
Alphanumeric—encrypted data is letters and numbers: a-z, A-Z and 0-9
Numeric—encrypted data is only numbers: 0-9
(Optional) Enable Encrypted with padding if the tag was padded before encryption. Padding may compromise the security or usability or protected data. Learn more.
Click Connect Tag.
You can decrypt format-preserving encrypted data in two ways: by creating a policy on the column or by using a user-defined function (UDF). The method you choose depends on how and when you need to access the data.
Create a Policy
Use policy to view decrypted data in the following scenarios:
Ongoing access management
Temporary access for specific users
Consistent enforcement across environments
Non-technical users maintaining access
Once FPE is set up for a column or a tag, set up policy to restrict access to the decrypted data. Learn more.
For example, if only ACCOUNTADMIN is allowed access to the data with No Mask, then
when an ACCCOUNTADMIN queries the data, they will see decrypted data (i.e., data in plaintext).
when a user with any role other than ACCOUNTADMIN queries the data, they will see encrypted data (i.e., data in ciphertext).
Use a UDF
Use a UDF to view decrypted data in the following scenarios:
One-time or ad hoc decryption, e.g., for a report or an audit
Permanently decryption a column, i.e., you’re no longer using encryption
Technical users maintaining access
To decrypt data using a user-defined function in Snowflake, run one of the following functions based on whether or not you have padding enabled:
If you have FPE and FPE padding enabled (learn more about padding):
ALTR_DSAAS_DB.ALTR_DSAAS_<ORGID>.ALTR_FPE_DECRYPT(CIPHERTEXT STRING, KEYNAME STRING, TWEAKNAME STRING, ALPHABET STRING, HAS_PADDING BOOLEAN)
If you have FPE enabled but not FPE padding:
ALTR_DSAAS_DB.ALTR_DSAAS_<ORGID>.ALTR_FPE_DECRYPT(CIPHERTEXT STRING, KEYNAME STRING, TWEAKNAME STRING, ALPHABET STRING)